Applies to the following Sophos products and versions Sophos Firewall Configuration First, verify the HTTPS scanning CA used by the XG Firewall. It can be found on XG webadmin Web General settings. To download and install the certificate in your browser and the local machine, follow the steps below. Download the certificate to your local. At some point I may want to get restrictive, but for now I'd like it open with return traffic related to those established and related connections permitted. So, this would be A on the diagram coming to Sophos XG on Port 1. I'd like the PC at B to be configured from a Sophos XG perspective in the same way as (1) above. Apr 12, 2021 18. ) Running Certbot with the certonly command will obtain a certificate and place it in the directory /etc/letsencrypt/live on your system. In case you have own SSL certificate you want to use, simply place the files into the Weblate data volume (see Docker container volumes ): ssl/fullchain. Go to Rules and policies Firewall rules. Select IPv4 or IPv6 and select Add firewall rule. For Action, select Protect with web server protection. To create a WAF rule, set Preconfigured template to None. You will use this Public and Privatkey certificate. There are couple of approaches to upload this to XG. The first LE Cert can be simply uploaded. You should use the Public.pem in 'Certificate' and the Privatkey in 'Privat key'. PS: you have to rename the Privatkey.pem to Privatkey.key, otherwise XG will not take this certificate.
Here at Naked Security, we’re well-disposed towards encryption, especially TLS, which is the cornerstone of secure web browsing.
TLS is short for Transport Layer Security, and it’s the technology that puts the padlock in your browser’s address bar when you use HTTPS to visit a secure website.
In theory, TLS is easy, because software at each end does all the hard cryptographic work of securing the connection.
Importantly, TLS isn’t only about the confidential aspects of encryption, where your data is scrambled so it’s meaningless to eavesdroppers.
TLS also deals with authenticity and integrity, using encryption to help you verify not only that you’re talking securely, but also that you are talking to the right person.
(No point in having a strongly-encrypted session with a crook instead of your bank!)
But TLS has one tricky part: before your web server can “prove” who you are, you have to get a digitally-signed certificate that vouches for you, issued by someone who is themselves trusted by everyone’s browsers.
Understanding HTTPS and the “chain of trust” ►
Until recently, that was modestly complicated, and cost money, both up front and then every year or so to renew the certificate.
Then, a non-profit called Let’s Encrypt came on the scene:
Anyone who has gone through the trouble of setting up a secure website knows what a hassle getting and maintaining a certificate can be. Let’s Encrypt automates away the pain and lets site operators turn on and manage HTTPS with simple commands. Using Let’s Encrypt is free, so there is no need to arrange payment.
The concept is simple: HTTPS makes things harder for eavesdroppers, phishers, scammers and other imposters, so let’s encrypt.
An imperfect month
Unfortunately, the past month hasn’t been a perfect one for Let’s Encrypt.
Back in May 2016, the organisation let slip a login key for its GitHub account, where the source code used to run the service is hosted.
In theory, that meant anyone who’d noticed the leaked key could have logged in and made unauthorised changes deep inside the codebase, undermining the trust in the community that has sprung up around the project.
A security breach, even a potential breach that fortunately never happened in real life, is never a happy moment.
But the Let’s Encrypt team responded quickly and openly, and concluded:
Our investigation has concluded, and with GitHub’s help we’ve determined that the leaked credentials were never improperly used. No code was improperly modified, and no subscriber or other confidential information (aside from the leaked API key) was exposed.
A good outcome under the circumstances.
Another security SNAFU
This weekend, Let’s Encrypt had another security SNAFU, this time involving leaked email addresses.
To be fair, leaking email addresses, for example by CCing people when you meant to BCC them, isn’t the end of the world, but it’s still something best avoided.
Spreading big email lists to very many recipients isn’t just a breach of privacy, it’s also a potential gold-mine for spammers.
Malware on any one of the computers that received the list could scoop up those addresses and “call home” to deliver them to the crooks, perhaps leading to yet more spam for the innocent names in the list.
What happened with Let’s Encrypt was nearly, but not quite, amusing:
- The first person received an email containing the message body.
- The second person received an email containing the first person’s address plus the message.
- The third person got the first two addresses plus the message.
And so on.
If Let’s Encrypt hadn’t noticed early on, the last person would have received 382,999 addresses plus the message.
The good news is that the glitch was noticed after 7618 messages and the plug was pulled on the process.
Note that 1+2+3+4+5...+Ncomes out as N/2 × (N+1), which is (N2 + N)/2, which grows quadratically with N (i.e. “as its square”).
Let’s Encrypt may have spotted them problem because this sort of quadratic growth in the total volume of email going out is rather unusual.
Ironically, perhaps, the email was to tell subscribers about an update to the subscriber agreement.
As the organisation said:
We take our relationship with our users very seriously and apologize for the error. We will be doing a thorough postmortem to determine exactly how this happened and how we can prevent something like this from happening again. We will update this incident report with our conclusions.
If you received one of these emails we ask that you not post lists of email addresses publicly.
The silver linings are that the problem was stopped early on, and that Let’s Encrypt’s apology carries some weight.
They’ve promised to report how the mistake happened, and how to stop it in future, which is actually both open…
…and useful, because we can all learn from other people’s mistakes.
Security tip. An email gateway with some form of DLP, short for data leakage prevention, can help in cases like this. For example, using the Sophos Secure Email Gateway, you can use what we call content control lists to set a rule such as “no outbound email should have more than 10 plaintext email addresses” (or any credit card numbers at all, and so on). This limits the damage done if a user copies-and-pastes the wrong data, or an automated script goes haywire.
Having a small home lab I wanted to be able to setup internal services, and then on the go be able to access them. While I could setup a L2TP or SSL VPN and connect whenever I wanted to use these services, I thought I would give On-Demand VPN via a iOS/macOS configuration a try. Little did I know the world of hurt I was entering. I will start with the settings you need to get it working, since a lot of people just want that. Then I will talk about the crazy and painful road I went down before finding 1, just 1, set of settings that seem to work. If you have any questions, thoughts, or success stories please comment below!
Fun fact: I will be calling the protocol IPsec here. That is what the original RFC called it, what the original working group was called, and the capitalization they used. Sophos agrees and uses that capitalization, while Cisco and depending on which web page you are on for Microsoft may call it IPSEC or IPSec or IPsec.
On-Demand VPN gives you the ability to set certain websites or IPs, and when your phone or laptop attempts to connect, the machine silently brings a IPsec tunnel online and uses it for that traffic. This allows you to run services at home, and to users (your mom or cat or whomever) it looks like just another website. Apple has 1 big requirement for them, you have to use certificate based auth. You can not use a pre-shared key/password. Also up front, to save you a few days of trying things. iOS and macOS will NOT check your certificate store for your VPN endpoint (Sophos XG) certificate, it HAS to ship with the firmware or you will get the fantastic and descriptive “Could not validate the server certificate.” Also believe it or not, that is one of the most descriptive errors you will get here. There are some posts on the Apple support forums from Apple engineers saying the root CA has to be in already on the device. If anyone gets it to work with your own let me know.
Sophos XG Setup
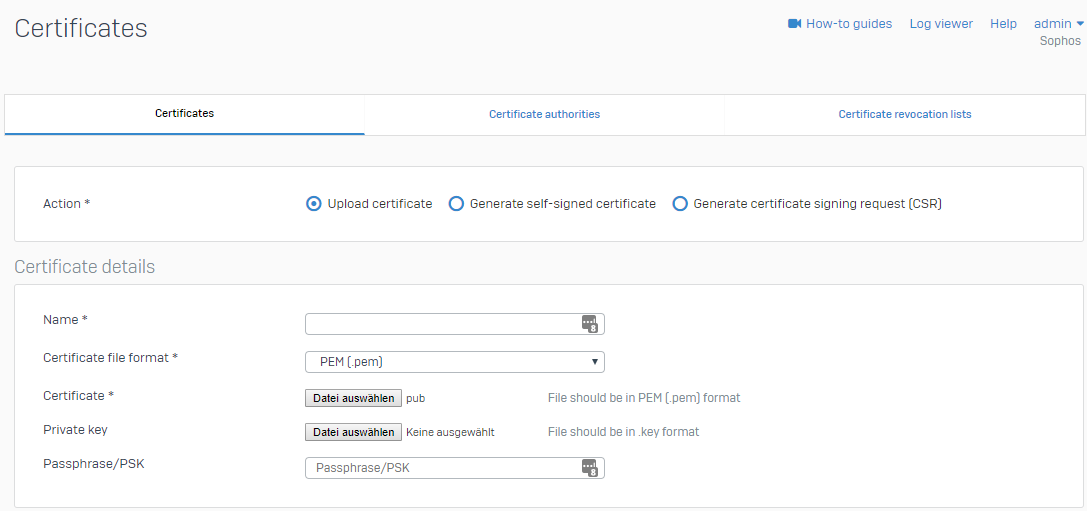
I am using Sophos XG v18 with a Home license, backed by AD running on a Dell Optiplex for this guide (dont worry it as a cool Intel Nic in it). To setup the IPsec server in Sophos XG first we need to make 2 certificates. Login to the admin portal, then on the bottom left select “Certificates”. You need 2 certificates; 1 is our “local certificate” (we will call it Cert-A) this is a cert that is used for the server (Sophos) end. As previously mentioned, this has to be a real signed cert. I ended up forwarding a subdomain on my site to the firewall, and then using Let’s Encrypt to create a cert for that URL. I used this site, https://hometechhacker.com/letsencrypt-certificate-dns-verification-noip/ to guide me in creating the cert on my laptop, then I uploaded that to the Sophos firewall. This will require you to have access to your domains DNS settings or be able to host a web file.
The second cert (Cert-B) is for the client, Sophos will call it “The Remote Cert”; this is to auth to the firewall, that can just be a locally generated cert. All devices will share this cert. The devices will use their username and password combination to identify the user. I used email as the cert ID, note this email does not have to exist, I just made one up on my domain so I will know what this cert is. Once created, go back to the main Certificates page and download the client/remote certificate, I suggest putting an encryption password on it since the Apple tools seem to freak out if that is missing. But ALSO the password for this cert will be in clear text in your config, so don’t make it a password you care about. These certs all need to be rotated at least once a year, with the newer requirements; Let’s Encrypt is every 90 days and I intend on automating that on one of the Linux machines I have.
Now that we have our 2 certificates, lets go over to “VPN” on the left hand navigation. I have tried many settings in the main “IPsec Connections,” and none of them have worked for me. I get fun and generic errors from the Mac of “received IKE message with invalid SPI (759004) from other side” or “PeerInvalidSyntax: Failed to process IKE SA Init packet (connect)”.
Click the “Sophos Connect Client” tab, the back end of this client is just a well setup IPsec connection. Fill in the form, from the external interface you want to use, to selecting “Digital certificate” as your auth method, followed by the “Local certificate” which is the Let’s Encrypt one (Cert-A). “Remote certificate” is the one we will load on your device (Cert-B).
Now you select which users you want to have access to use this. I have Active Directory backing my system, so I can select the AD users who have logged in before to the User Portal. This is a trick to Sophos XG you may need, if you use AD and a user doesn’t show up, that means they need to login to the User Portal first.
Untangle Letsencrypt
Select an IP range to give these clients, I suggest something outside any of your normal ranges, then you can set the firewall rules and know no other systems are getting caught in them. Once you are happy, or fill in other settings you want like DNS servers, click “Apply”. After a second it will activate, you can download the Windows and Mac client here, or follow along to make a profile.
Apple Configuration
To create a configuration file you need to download Apple Configurator 2, https://apps.apple.com/us/app/apple-configurator-2/id1037126344 onto a Mac. I know what you are thinking, 2.1 Stars, Apple must love enterprises. Download that from the store and open it up. If you do not have a Mac I attached a templatethat you can edit as a text document down below. This profile needs a Name, as well as an identifier. The identifier is used to track this config uniquely, if you update the profile, then your device will override old configs instead of merging. You will see on the left there are LOTS of options you can set, the only 2 week need are “Certificates” and “VPN”.
Starting with Certificates, click into that section, then hit the Plus in the top right. Upload the cert we exported from Sophos (Cert-B) earlier for the end device, and enter the password for it. Again note, this password is in plain text in the config file.
Now for the VPN Section. Click the Plus in the top right again to make a new profile, name the connection anything. Set the Connection Type to “IPsec”. IKEv2 is IPsec but a newer version, I will get into some of this later after our config is done and I can rant. Server is your Sophos XG URL. Account and password can be entered here to ease setup, or you can leave one or both blank to make the user enter it when they import the config. You can leave the user/password fields blank (it will give you a yellow triangle but that is fine) and then give it out widely and not have your creds in it… For “Machine Authentication” you want “Certificate”; you will see in selecting “Certificate” all of a sudden the On-Demand area appears. For “Identity Certificate” select the one we uploaded before. Finally we can enable “Enable VPN On Demand” and select the IPs or URLs you want to trigger the VPN.
Once that is done, save the profile and open it on a Mac or you can use this configuration tool to upload it to an iOS device. That should be it! Your devices should be able to start the connection if you ask it, and if you go to the website should auto vpn. Make sure you have firewall rules in Sophos XG for this new IP range, or that can block you from being able to access things.
A small note, from my tinkerings with the On Demand profile if you go to Safari on a iOS device, it will connect when you visit a website that is in the configuration. If you use a random app, such as an SSH application, I didn’t find it always bringing the tunnel up, and at times it had to manually be started. Something to lookout for, a nice part of the the IPsec tunnel is that it starts quickly.
Sophos Xg Let's Encrypt Download
Now that the config is done, I want to mention some of the other things I have learned in tinkering with this for several days. The only way I got it to work is using that Sophos Connect area, and the other big not documented thing is you have to use a publicly trusted cert for the Sophos end. I found 1 Apple engineer mention this on their forum, and a TON of people talking about how they couldn’t get the tunnel to work with their private CA. I have tried uploading a CA, and injecting it different places with different privileges for the Mac and never could get it to work. The Let’s Encrypt cert imminently worked.
For IPsec v1, aka IKEv1, Apple uses the BSD program racoon on the backend to manage the connection. Using the “Console” app you can find the logs of this. For IKEv2 it seems Apple wrote their own client around 2016-2018, there are a lot of reports online that it just doesnt work at all with cert based auth. All the guides about it working stop around 2016. You can find earlier ones, or people using pre-shared keys, but selecting pre-shared keys doesnt allow us to do a On Demand VPN. The bug has been reported for a while, https://github.com/lionheart/openradar-mirror/issues/6082. If you try to do this, you can expect A LOT of “An unexpected error has occurred” from the VPN client. Even looking at the Wireshark traffic didn’t lend any help on tuning Sophos to give the IKEv2 client something it would accept. If someone figures out how to get that to work in this setup please let me now.
Now that everything is setup you can host things yourself. I give the auto connecting VPN less rights than when I do a full tunnel on my laptop, but it allows for things like Jira to be hosted, then mobile clients to easily connect.
Template
Sophos Xg Let's Encrypt The Password
For your cert to work in the template it needs to be converted. Sophos will give you a .p12 file for your cert, use the following command to get the version that needs to be in the .mobileconfig file. You’ll at minimum want to edit the cert area and put yours in there, set the password for the cert, and any URLs you need.




